Configure SSO for your status page with Okta
In order to configure a SAML application for Statuspal in Okta head out to your Okta admin panel and follow these steps:
Click on Applications then click on Create App Integration.
Check SAML 2.0 and click on Next.
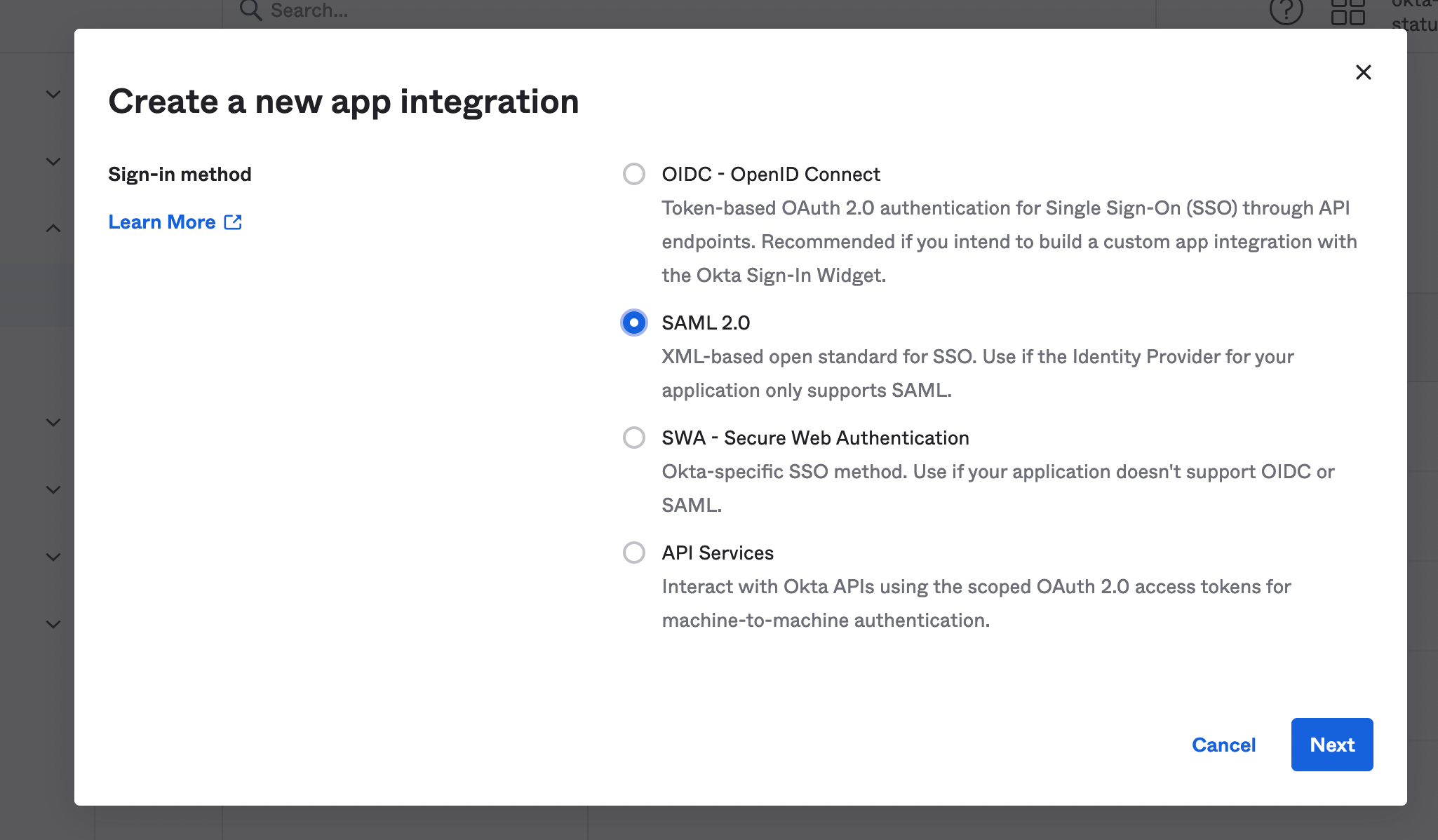
Enter the App Name statuspal.io and click on Next.
Copy the ACS URL into Single sign on URL.
Copy the SP entity ID.
Click on Show Advanced Settings and check the "Enable Single Logout" field (to allow application to initiate Single Logout).
Copy the Single Logout URL.
Download the SP certificate and upload it into the Signature certificate, then click on Upload Certificate (in Windows you might need to use Edge for this step).
Scroll down and click on Next then click on Finish.
On the Assignments tab, make sure to assign yourself (the email you're signed in with in Statuspal) so you can test the configuration.
On the Sign On tab, Click on View Instructions and scroll down to find the IDP metadata then copy this into your organization and Save it.
Click Save, then Test SAML configuration, it should success and look like this.
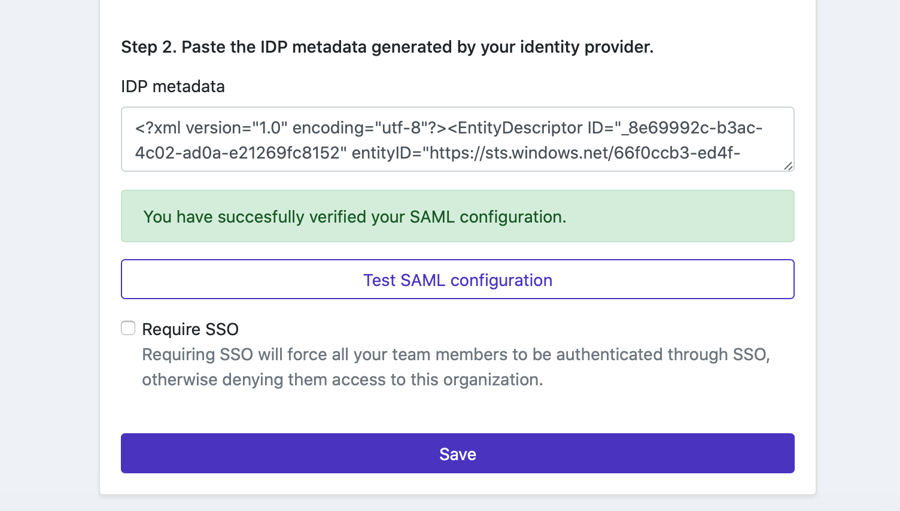
After successfully testing your SAML configurations you should be able to check the Require SSO field, which will cause all your team members to be required to be authenticated with SSO before accessing the organization.
Last updated